2018 started with a bang!
In the first days of January researchers discovered a couple of security vulnerabilities that affect nearly every laptop, phone or other server using processors produced by very well-known hardware providers.
The hardware bug, which can lead to two different vulnerabilities called Meltdown and Spectre, if exploited, allows the attacker to leak data from memory. Both attacks break the isolation layers between user application and operating system. These cracks can be used by malicious attackers to steal/expose sensitive information, such as passwords, personal photos and any other user-specific details.
Let’s focus for a moment on the names the researchers who discovered these issues picked for them: Spectre and Meltdown. They explained that Spectre was so-named because “As it is not easy to fix, it will haunt us for quite some time”; Meltdown was chosen because “vulnerability basically melts security boundaries which are normally enforced by the hardware”.
Luckily patches to fix both bugs have been released, but they come with a performance cost.
Most companies have run benchmarks to measure performance changes before and after the solutions to these security vulnerabilities were applied. And so did we.
We tested our software on a 4-core machine with the following specs:
- Intel(R) Xeon(R) CPU E5-2630 v2 @ 2.60GHz
- Ivy Bridge, 2013, 22nm
- Linux 3.10.0-693.11.6.el7.x86_64
- CentOS Linux release 7.4.1708 (Core)
We have considered four different testing scenarios involving the latest Varnish Plus and our newest product addition, Varnish Total Encryption. For each of them we ran 100 trials using:
- 100k object size
- Malloc storage
- 90/10 hit-miss ratio
Tests and results
Test 1: Varnish Plus running on the above-mentioned hardware with no Kernel Page Table Isolation (which we’ll call KPTI from now on) patch, which is a new kernel feature released to mitigate the Meltdown and Spectre vulnerabilities.
Test 2: Varnish Plus running on the same hardware after applying the KPTI fix.
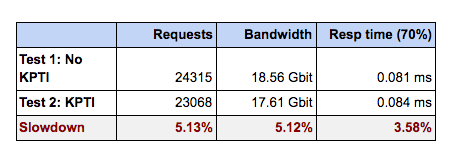
As illustrated in these results, the KPTI fix adds about 5% overhead to Varnish, which we consider to be a very good result especially given the nature of the patch.
We then stretched our benchmark a little bit more, testing our software while using Varnish Total Encryption, a solution recently released from the Varnish lab and introduced here. In my humble opinion, Total Encryption is a must-have to secure your users’ data. It is a cache encryption that assigns each object in the cache a unique encryption key, making it next to impossible to use any of the cached content in the unfortunate event of a malicious attack.
Test 3: Varnish Plus with Total Encryption enabled and no KPTI patch applied
Test 4: Varnish Plus with Total Encryption enabled and KPTI patch applied
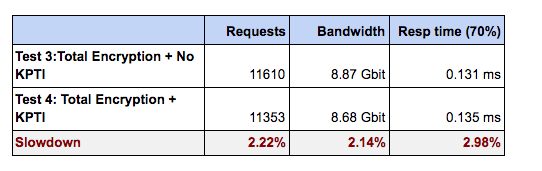
Again, the overhead introduced by the KPTI is quite low, as it stays below 2.3%, which proves to be another awesome result.
Conclusions
This graphs illustrates better how the KPTI doesn’t really affect performance in Varnish. We therefore conclude that we expect our solutions to run as smoothly as usual with or without the KPTI fix.
Varnish Total Encryption requires 50% more CPU to have the same performance as regular Varnish solutions, but that’s a small cost to safeguard your cache infrastructure and the data it handles.
You can learn more about encrypting your cache to safeguard your data - and more about compliance with GDPR data processing and handling regulations - in our upcoming live webinar (February 13), "How to make your cache infrastructure GDPR compliant".
/VS-logo-2020-197x60.png?width=136&height=60&name=VS-logo-2020-197x60.png)




