The transition to internet protocol version 6 has opened up a whole new range of threat vectors that allow attackers to set up undetectable communications channels across networks, researchers have found.
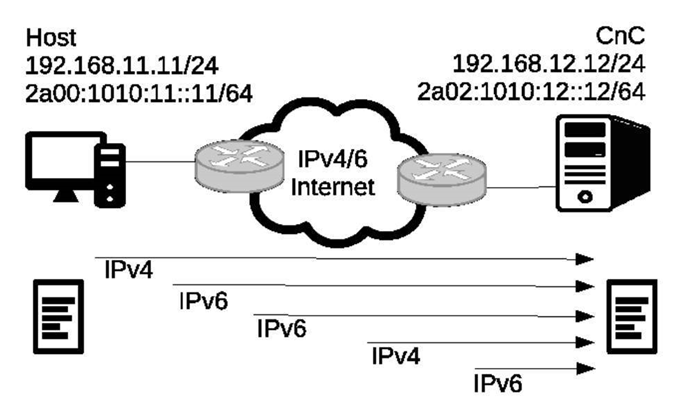
A paper has been published by researchers at the NATO defence alliance's Cooperative Cyber Defence Centre of Excellence and Estonia's Tallinn University of Technology. It outlines how attackers can create covert data exfiltration channels and system remote control, using IPv6 transition mechanisms.
IPv6 aims to remove the technical drawbacks of the older IPv4 addressing scheme but brings its own fresh set of dangers, the researchers warned.
Since IPv6 implementations and security solutions are relatively new and untested, and systems engineers aren't fully aware of them, the new protocol can become a network backdoor attackers can exploit undetected.
The researchers developed proofs of concept with tunnel-based IPv6 transition tools over IPv4-only, or IPv4/IPv6 dual-stack networks, that were able to pass traffic undetected by common network intrusion detection systems (NIDS) such as Snort, Suricata, Bro and Moloch.
Defending against such IPv6 tunnelling attacks is very difficult with current NIDS.
"... any reasonably sophisticated method for exfiltrating data will be hard to detect in real-time by existing NIDSs, especially in situations where the data is split into smaller chunks and the resulting pieces use different connections or protocols (e.g. IPv4 and IPv6)," the researchers wrote.
Fundamental changes to the way network traffic is interpreted and parsed are required to address the threat, and administrators need to know how to properly configure, deploy and monitor security solutions to be aware of network flows, the researchers said.


















.png&h=141&w=208&c=1&s=1)

